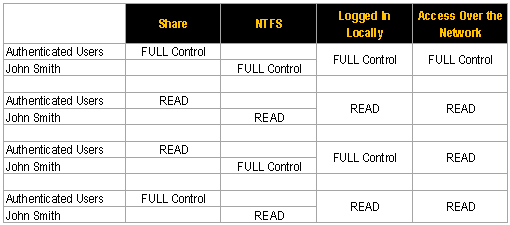
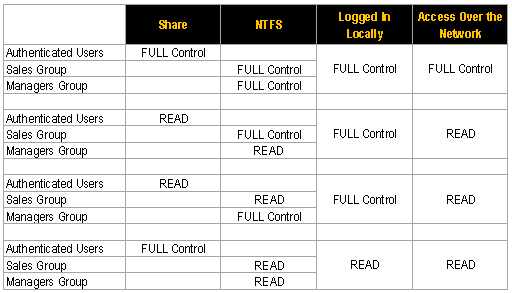
The SHARE permissions determine the type of access users have to the shared folder when the resource is being accessed over the network. SHARE permissions are not evaluated when users are logged into the resource locally. There are three types of share permissions: Full Control, Change, and Read. NTFS permissions determine the action users can take for a file or folder when accessed locally. When both permissions are in place, the most restrictive permission will be applied to the user accessing the resource. If you are logged on a computer locally, the SHARE permissions applied to a folder have NO impact on the user. In a scenario where the user is logged on locally, only the NTFS permissions are evaluated. If you are accessing a resource (file, folder, etc.) over the network, then you combine the SHARE and NTFS permissions. The most RESTRICTIVE permission is the effective permission. As a general rule, it is an acceptable practice to set the SHARE permissions to Authenticated Users/Full Control and manage the permissions via the NTFS Security tab. Whatever permissions you set in the Access Control List (ACL) will take effect since the NTFS permission will be equal to or more restrictive than the permissions defined in the SHARE tab. Here is a simple example to help you better understand how SHARE and NTFS permissions impact the user accessing the resource. In this example, John Smith is the Authenticated Users group. Permissions are applied to the Authenticated Users group at the SHARE level and NTFS permissions are applied to John Smith directly. Of course in realistic environments, permissions can become more complex. You will most likely find that different permissions are applied to more than one group. Users can be and are generally members of multiple groups. In scenarios such as those, permissions are first COMBINED at each level (SHARE and NTFS) when users are members of multiple groups. Then, secondly, the most RESTRICTIVE permission is applied. In this example, John Smith is a member of both the Sales group and Managers group. If you have grasped this basic concept, you’ll find that it will be easy to determine a user’s effective permission applied to a resource. Hopefully, this summary has clarified it for you.